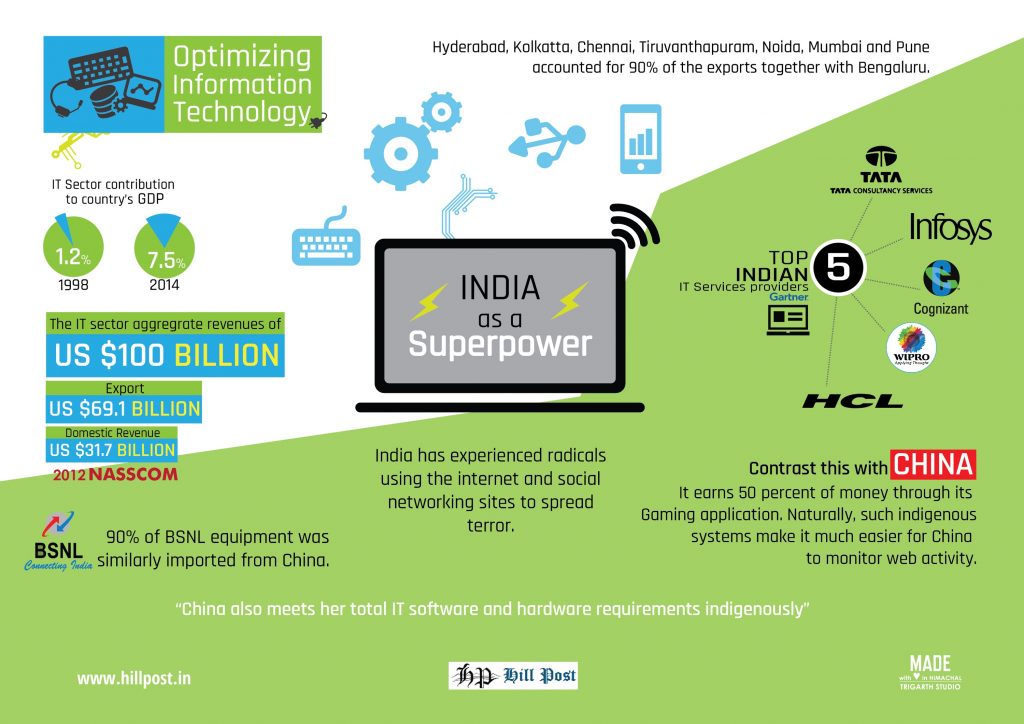
 More than two years back on November 2012, UN Secretary General Ban Ki-moon praised India as a “superpower” in the field of information technology as he unveiled the India’s first indigenously created low-cost Akash2 tablet made by Datawind.
More than two years back on November 2012, UN Secretary General Ban Ki-moon praised India as a “superpower” in the field of information technology as he unveiled the India’s first indigenously created low-cost Akash2 tablet made by Datawind.
Ban Ki-moon said, “India is a critical player on security issues, but you are also a leader in development and technology. Indeed, India is a super-power on the information superhighway. There is a reason places like Hyderabad are called Cyberabad.”
In India, the IT industry can be broadly classified in two major segments; first IT Services and the second, business process outsourcing (BPO). The IT Sector contribution to the country’s GDP was 7.5 percent as compared to 1.2 percent in 1998. According to NASSCOM, the sector aggregated revenues of US$100 billion in 2012, where export and domestic revenue stood atUS$69.1 billion and US$31.7 billion respectively, growing by over 9 percent. Exports dominate the industry and constitute about 77 percent of the total industry revenue. However, the domestic market is also significant with a robust revenue growth. The industry’s share of total Indian exports (merchandise plus services) increased from less than 4 percent in FY1998 to about 25 percent in FY2012. According to Gartner, the top five indian IT services providers” are Tata Consultancy Services (TCS), Infosys, Cognizant, Wipro and HCL Technologies.
While Bengaluru was known as Silicon Valley of India since long being leader of IT exports, other cities like Hyderabad, Kolkatta, Chennai, Tiruvanthapuram, Noida, Mumbai and Pune accounted for 90 percent of the exports together with Bengaluru.
That information and communication technologies are transforming lives in India is visible across the board. However, it is also known that our progress in IT has been more in the software field while bulk of the IT and telecommunications equipment is being imported. In fact till about 2008 even old companies like Wipro were only assembling computers in India with 100 percent parts imported from China even without the ability to check for malware that may have been embedded at manufacture stage.
Again, 90 percent of BSNL equipment was similarly imported from China.
Even items like pen drives continue to be imported from abroad. As far as cyber security is concerned, India’s focus has improved over the past four years or so but we still have a very long way to go.
The recent incident of discovery and apprehension of Mehdi alias Shami Witness from Bengaluru (the Silicon Valley of India) itself has brought into sharp focus the dangers of use of social networks by terrorists and radicals.
The fact that Mehdi (the ISIS Twitter handle) was active since 2003 but our intelligence agencies got the wind of him only after his discovery was reported by UK’s Channel 4 News is an issue of serious concern.
As per Channel 4, Mehdi’s tweets, written under alias Shami Witness, were seen two million times each month, making him perhaps the most influential ISIS Twitter account, with over 17,700 followers. On Twitter, his account was reportedly also followed by jihadist fighters and Middle East analysts. It is also quite possible that the false news of rapes and photos posted on social media one year back of homes attacked and burnt that forced the exodus of northeast youth working in Bengaluru and Delhi was handiwork of Mehdi or other radicals.
Similarly, the Whatsapp message purportedly by a young officer post the recent terrorist camp on an army camp in Uri may well have been by radicals aimed at creating dissension in the army’ rank and file.
This is not the first time India has experienced radicals using the internet and social networking sites to spread terror. Our intelligence agencies had reported earlier that IM cadres had been using proxy servers and complex code to chat: setting up email accounts that disappear if they not accessed in 24 hours, proxy servers to camouflage geographical location, encrypted files and complicated code language; use of US-based Yahoo Inc, Paltalk Inc, Sophidea Inc and Hurricane Electric, plus providers in Nepal, Canada and Ireland; IP address of Nimbuzz chat traced to Pakistan Telecom Company Ltd and others traced to France, Germany, Netherlands, Nepal and India.
Additionally, Riaz Bhatkal and his close aides are known to run a hi-tech command centre in Karachi to communicate with terror cells in India and Nepal, and possibly even Maldives in Sri Lanka and Bangladesh.
However, in the case of Mehdi (the ISIS Twitter handler), it is significant to note that Twitter India when questioned replied, “We do not comment on individual accounts, for privacy and security reasons. We do not proactively monitor content on the platform.
We review all reported accounts against our rules, which prohibit direct, specific threats of violence against others.” You cannot really fault Twitter or any other social networking site to reply differently.
So the question is where do we go from here?
The Videsh Sanchar Migam Limited (VSNL) had introduced Gateway Electronic Mail Service as far back as 1991, the 64 kbit/s leased line service in 1992, commercial Internet access on a visible scale in 1992 and the 1992 election results were displayed via National Informatics Centre’s NICNET.
But what have we done to develop our own operating systems, our own social networking sites and gaming applications etc?
Contrast this with China.
The top level Chinese IT company like Tencent (qq.com) established only in 1998 and listed number 4 of 100 top internet companies by Forbes in 2014 offers equivalents of Skype, Facebook, Twitter, Amazon, Microchat, Wizard, Google, Gaming etc and claims improvement over Twitter. It’s V-chat (equivalent of Whatsapp) being used in 00 countries.
I’m It earns 50 percent of money through its Gaming application. Naturally, such indigenous systems make it much easier for China to monitor web activity.
Then China also meets her total IT software and hardware requirements indigenously.
These are issues of serious concern that require holistic appreciation, a comprehensive plan and a timed road map for execution. Without doubt a national level effort integrating the private sector and government entities is needed.
Prakash Katoch is third generation army officer hailing from Himachal Pradesh. He is former Lieutenant General from Special Forces and post-retirement has published over 2100 articles on international affairs, geopolitics, military, security, technical and topical issues besides authoring two books. He is active in seminars at both national and international levels.



